Analyzing the Malware... Kinda
In the spirit of getting better everyday I downloaded some malicious files from the site www.virusshare.com and am going to be spending some time playing around with them. I'll be using my REMNux VM and seeing what all I can figure out. Follow along for some beginner moves and learn with me along the way! Find the walkthrough video below and enjoy.
Startup
First off I am going to be using REMNux, and while there are certainly other options this is the one I'm using for now. Feel free to use whichever you prefer, but to best follow along with me REMNux is going to be what you want to use. I have a tutorial written up for the install, and you can find there here: https://jrhacka.github.io/post/remnux_setup/
Once you spin up REMNux go ahead and head to www.virusshare.com. Just an FYI you will have to create an account, but it's a simple process and just use a "throwaway" email in case it does start to spam you with items. It does take a few moments for them to email you your username and password, but once that is done come back and we can pick up where we left off.
I created this account one week plus some before posting this article, and have not noticed anything malicious. Just in case be sure this isn't your main email.
Once that is done you can login with your username and password. From there select the option Torrents up at the top of the page. The file I seleted was the item at the top of the list, and called VirusShare_00000.zip and was 13.56GB. If it is not at the top of the list anymore I am so sorry, but the best thing I can think to tell you is find the file with that name. If they changed names... match the sizes...?
So once you get that file you're going to want to use qbittorrent, or something like it, in order to get the actual zip file. If you do not have qbittorrent you can install it by running:
1sudo apt install qbittorrent
Once you have that on go ahead and right click the downloade torrent and use open with qbittorrent. Once you have the zip file hop back into the command terminal and run:
1unzip file/path/here
The REMNux terminal isn't the greatest. I would be sure and install terminator to make your life a little bit easier.
Organization
So now you have an absolute ton of greate malicious file examples to dive into. The key in this, and really anything, is going to be reamining organized. I made a new directory called WorkingMalware. In that directory I also created a InProgress and Comp subdirectory. You can name or organize however you want, but just be sure you have an A(file from virusshare)-->B(In progress)-->C(Finished) methodology. That way you can keep track as you work through them. The file I used for this analysis was VirusShare_fff3093fe6a763b588b51479f6f52a24. I copied it from it's place in the virusshare folder to the InProgress directory in a directory titled the date 081022. I am going to use the 081022 folder to store all the data I generate for this malicious file. Now it's time to dive in.
VirusTotal and Strings
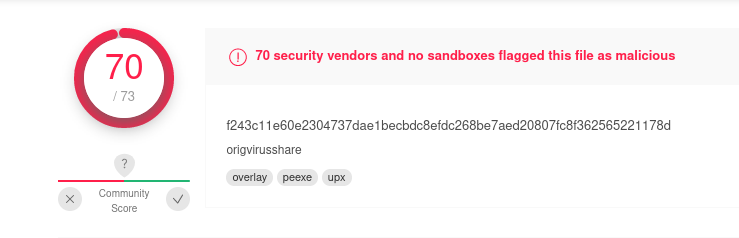
So the first thing I'm always going to do is drop the file in www.virustotal.com and see what it gives me. When we drop our file in VirusTotal the site lights up like a Christmas tree. We can now confirm that this file is indeed malicious... lol.
The second thing I always do is probably very much up for debate. I learned this from John Hammond, and I do like to at least see what strings and file will tell me.
1file filename
2strings filename
From that we pick up two important things. File tells us that this is a PE32, which is a 32-bit portable executable, and that it is compressed using UPX. We can confirm that by running strings and seeing the UPX0 and UPX1 right at the top. We can decompress the UPX by running the following:
1upx -d filename -0 newfilename
We can run strings on that again and we see a lot of stuff, but my newbness came in to play very quickly.
In Conclusion
You will certainly see a part two for this down the line. I'm pretty booked up in the next couple weeks, so this is not goodbye but see you later. Myself and VirusShare_fff3093fe6a763b588b51479f6f52a24 will meet again.